Hackers today employ a number of innovative ways to secure private data including phishing, Trojans or denial of service (DOS) attacks. Each attack becomes a little more creative than the last, which puts a user’s sensitive data at risk. When it comes to servers and unsecured network data in the wrong hands, it will also hurt your reputation and financial stability which leads online users to question if a virtual private network (VPN), proxy server, anonymous network or Remote access services (RAS) is better for cybersecurity. In this article we will discuss the differences between proxies and VPNs explained in terms that anyone can understand.
VPN Advantages
Should I Use A VPN? The Pros & Cons
VPNs enable users to access networks securely and share data privately. Just as your firewall protection on your computer safeguards your data, VPNs do the same job online. While it is true that a VPN is a technically a wide area network (WAN), it maintains the security, appearance and capabilities of a private network, which is why the usage is so popular by those who want to secure an access point because they have both encryption codes and dedicated connections which promotes security and blocks direct access to data. VPN security measures include internet protocol security (IPSec), layer 2 tunneling protocol (L2TP), secure socket layer (SSL), transport layer security (TLS), point-to-point tunneling protocol (PPTP) and secure socket shell (SSH). The benefits include:
- Security: Cybersecurity is one of the most prominent challenges online. Anytime you are connected, you are susceptible to attacks because hackers are targeting users with viruses, malicious programs and phishing scams in which interception is key.
- Privacy protection: From advertising based on your searches to data mining, your privacy is always at stake. Whenever your devices are connected, your information like IP address and personal consumer behaviors leave traces of your activity on the pages you visit.
- Connectivity: If your internet service is limited in its capacity, using a VPN enables you to use a secondary location to route traffic which hides your location from the sites you visit.
- Fast, free and great for peer-to-peer (P2P) file sharing: There are some disadvantages to using a VPN provider as your activity is accessible. VPNs are also susceptible to legalities, which include open access to law enforcement that request logs.
Alternatives to VPNs
1. Proxy Servers
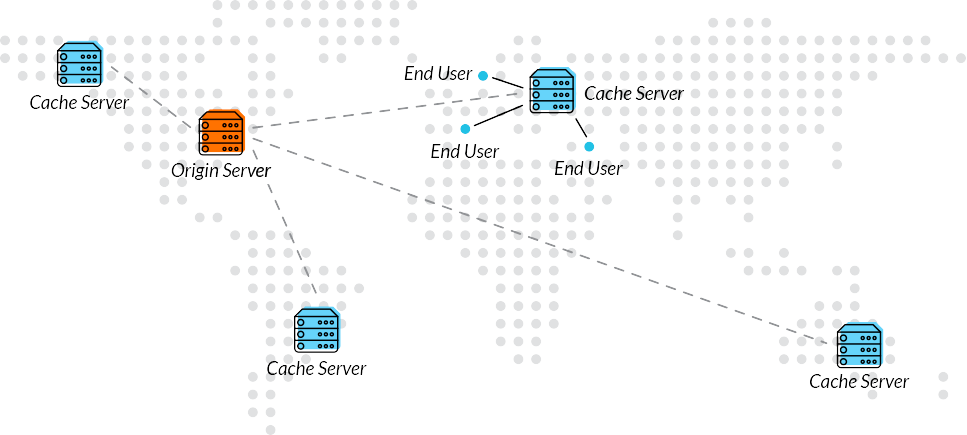
What Site Owners Should Be Asking About CDNs
A proxy server and a VPN both connect remotely to computers, right? Not really, as a proxy allows you to connect to a computer online, which redirects your activity. Your computer sends a request to an internet service provider (ISP), and then sends the request to a proxy server. The proxy then sends the request to the website by using the IP address in your profile, which hides your real location. Proxy types include anonymous, high anonymous, transparent and distorting. The benefits include:
- Security: Proxies increase security levels that are not in place with Wi-Fi or direct IP internet access. It also allows users to connect to websites where restrictions are in place.
- Privacy protection: Proxy servers enable users to protect data from hackers because it bypasses access and uses more secured modes of connectivity to protect user’s data and privacy.
- Connectivity: Proxies are known to speed up accessibility so that it makes browsing more user-friendly because of cache systems. It allows you to access sites quicker than with IP access.
There are some disadvantages to using a proxy server. Cache systems can be accessed by providers. Your data is also at risk as information leaks occur using SSL or TLS connections.
Both a VPN and a proxy will hide the IP address of its users. VPNs encrypt your access and hide your location while proxies are not encrypted and act as a gateway that will secure the browsing activity.
2. Anonymous Networks
Using anonymous network software to access the internet https://www.wired.com/2014/06/be-anonymous-online/ is also another option to a VPN or proxy server. A VPN access will identify your IP address, but an anonymous network like Tor routes your access to different nodes, which only has access to the previous IP node address which disrupts the path of your device’s connectivity. As an anonymous network node is random, it is almost impossible to identify a path and provides a level of security for users.
- Non-traceable IP activity: The circuits reset after 10 minutes, which adds anonymity for users.
- Network distribution protection: Someone who is at risk for cybersecurity or needs to hide a location because of identity protection layers encrypted node access points.
- No cost for usage: Disadvantages include performance which is less accessible than a VPN or proxy server. It is not completely safe which still puts you at risk for cyber threats. Using multiple nodes also slows down streaming which is why many people sign up service.
3. Remote Access Services
Why You Can’t Forget to Monitor Your WAN
RAS include both software and hardware that enables users to access an internet connection remotely via a host network or computer. Normally, a user connects to a personal computer’s server via a dial-up connection. The PC connects to the server where the information requested is stored. The remote user then controls the keyboard and monitor, which uses commands to access the files. This is a common technique used by companies to troubleshoot technical issues, so there are many opportunities like TeamViewer for users to access applications. Benefits include:
- Accessibility: Employees who use remote access has direct access to company files which is critical when making decisions that affect a business’s financial landscape.
- Security: Companies secure the access via their servers, so they control the data that employees have access. It will protect files from external cyber threats.
- Privacy: When using a VPN or proxy, they are third-party sites which cannot guarantee protection from hacks or cyber threats. A RAS keeps file sharing secure.
- Low-cost maintenance: For large corporations, this type of remote access point is flexible for employees who do not want the hassle or cost of commuting to the office every day.
The disadvantage of using a RAS is that it requires several steps to secure a remote connection. If a company is experiencing downtime, there will be no server which will drive costs due to loss of productivity. Hackers also have the know-how to steal sensitive information.

Taking the time to learn more about accessibility will help users implement procedures that protect accessibility, connectivity, and usability, which will help deter cyber threats.