
Once upon a time, people used to talk about Apple Mac as if it were a magical kingdom where malware and viruses daren’t ever venture. Sadly, times have caught up with the Mac platform. Despite the fact that people still say things like “but I’ve had a Mac for 10 years and never had an antivirus: or a virus”, this should be taken with an enormous pinch of salt. Cause and effect don’t always correlate: and the reality is that people who use a Mac need to protect themselves just like everyone else. Particularly against the biggest threat of all. So, what has changed?
The professional’s choice

New Apple products have big growth potential
Firstly, people traditionally used Mac computers for business rather than pleasure: a fact that was all the more true ten years ago. People that use computers for business (whether it be for producing music, rendering film, using CAD packages, engineering, or architecture) are generally less likely to expose themselves to opportunities for getting malware. As such, if those people don’t get viruses it doesn’t necessarily mean that the golden Mac can be left to graze wantonly on the Internet’s pastures unchecked.
Usually, for one reason or another, professional people tend to buy, rather than pirate the software that they use. This, is just one example of how people might expose themselves less to malware (hidden in cracked software). The rise of Mac, however, brought the platform into the mainstream. The general public wanted a piece of its stronger security and the cult of Mac began. Cutting edge design and well marketed products such as the iPod and iPad, came with an addiction to Macintosh. Unfortunately, user habits among people that use a Mac for pleasure and entertainment can result in a higher risk of exposure.
The risk of connectivity

Social Media: A hunting ground for cybercriminals
In addition, the world has changed. Now, everyone is connected to the umpteenth degree. Social media and other forms of connectivity also increase the risk of exposure. Furthermore, general computing power and computing ability has improved. This, coupled with the rise of ‘script kiddie’ culture, has led to an explosion in hacking ability and opportunities.
Don’t get me wrong, the Mac platform did used to genuinely be safer. It is this fact that has led to the problem of people sticking their fingers in their ears while going na-na-na. Sadly, computing power and ability has closed the gap: and with the fruits of business waiting to be hacked the temptation to get into the Mac platform was always going to be massive.
Social engineering and the dreaded Trojan
How to remove Mac malware, viruses and ransomware for free | how to virus scan a Mac | how to avoid Mac malware and viruses
Time to get technical. The specific danger that Mac users face is perhaps one of the most frightening forms of malware of all: the Trojan horse. Trojans are an incredibly powerful form of malware that can give cybercriminals full control of the device that it is deployed on. This is achieved by taking remote control of the machine via a Command and Control (CnC) interface that communicates with a CnC server.
Trojans are nearly always introduced to a system due to human error. Phishing scams that make people click on a malicious link hidden in a message, on a website, or in an email. This is called social engineering and it is the most effective form of infection that there is. In fact – it is so effective and easy – that calling it hacking is almost as much of a fantasy as the Golden Mac itself.
So, how do you protect your Mac?

15 Mac-Hardening Security Tips to Protect Your Privacy
By their very nature Trojans rely on the user to infect themselves. With that in mind, being careful about what you click on is essential. Emails that have links in them can lead to infection, so if you don’t know the person sending the message, or the email (address seems dodgy): beware!
In addition, social engineering is designed to raise interest. So, it is possible that the email will be disguised as something in the industry that you work for. Funny or ‘hot people’ are another common form of infection so beware the social media contacts with a pretty face that you’ve never met: they might be after something other than a date.
Panic can also be used to make people click on links, so if you get an email that makes it seem like you have bought something that you know you haven’t: don’t necessarily click the link from the email to check. Go and check the Amazon, eBay, PayPal or your bank account first to see if it has really happened. In addition, please go and login independently, away from your email account – rather than following a link sent to you. Fake bank emails, for example, could make you hand over your details to a cybercriminal. Once they have your password they can get into your account.
Strong passwords
On the question of passwords, please make sure that they are strong and different for the various accounts that you own. This may be difficult in practice, because a strong password can’t easily be remembered (if at all) so use a password manager if needs be. That way you only have to remember one master password. Never forget: an easy password makes it too easy for a hacker to get into your accounts. Finally if you even suspect that you might have been hacked on any account or service: change your password at once and any other places that you used the same password.
Firewalls
A firewall is just as necessary on a Mac as it is on any other device. It stops unwanted people from connecting to your device, and in the very best instances from communicating unwantedly with the outside world.
A great example of a truly outstanding Mac firewall is LittleSnitch. The beauty of LittleSnitch is that it asks its user about outgoing communication requests. This helps protect against a Trojan (which communicates by secretly sending information back to a CnC server). With LittleSnitch, the user is asked if this connection should be authorised. As such, the firewall is excellent because it does exactly as its name suggests.
Flash and Java
These programs might make the Internet more fun, but the fact is that everybody knows that they are an infection route. Only recently, yet another Flash vulnerability came to light: making some people believe that Mac might stop allowing Flash on its machines eventually (Safari 10 does disable Adobe Flash by default). However, nobody is forcing you to run your Mac with Flash and Java installed – so if you want to keep your Mac free from malware – uninstalling them is an option.
Remember that Java is a runtime environment (RTE), so when you use it you are running a virtual machine on your Mac. Sadly, although it is supposed to be sandboxed, any flaws in that sandbox can be exploited by hackers. The problem with both Flash and Java is that they independently, and automatically, agree to run programs in their respective environments without asking the user permission.
“But I haven’t been hacked!” I still hear you saying
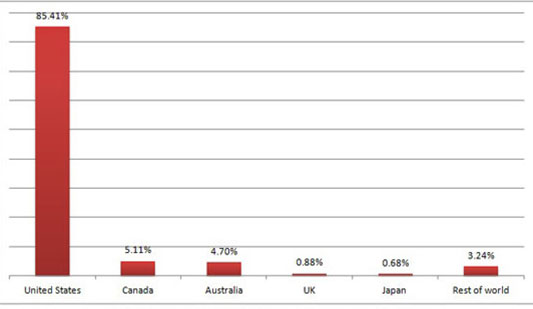
Cybercriminals Set Their Sights on Mac Users
Apple Mac is notoriously more expensive than its Windows PC counterpart. As such, the uptake of its machines is still lower. While there’s still worldwide growth of Macs versus PCs, the overall usage is still 7.4% of the worldwide PC market. This is a large reason why there has been less hacking of the Mac platform, so far.
Cybercriminals hack for financial rewards, and phishing in a sea brimming with Windows computers is easy pickings. However, hackers are realizing that they can extort larger rewards from wealthier Mac owners. As such, the problem is only likely to grow. Add to that, the fact that the once highly insecure Windows platform has become more secure and you have another reason why hackers might start to gravitate towards both hacking OS X.
Stop lying to yourself

Can Macs get viruses and malware? We ask an expert
Yes, it is true that OS X is based on the BSD Unix system, and that does means that the Mac OS is a sandboxed environment (it also means you’re a virtual guest on your own machine). It is also true that the latest instances of Mac have the GateKeeper function which stop Macs from installing software that isn’t approved by Apple. Having full control over its platform – and the Mac app store – does admittedly allow the firm to exert better control over what ends up on its machines.
Despite this, however, trends are going in the wrong direction and the general consensus is that Mac is vulnerable. Business Insider, even placed Mac OS X one place higher in its vulnerability scale than Windows 10 in 2016 (with 43 more vulnerabilities than Microsoft’s platform). In addition, malware has been found that locks up Mac computers: considering the cost of a Mac, this is rather concerning. The IT industry understands the problem all too well and they are talking about it regularly, so the time to stop being unnecessarily elitist has come to an end.
The good news, is that there are plenty of excellent antivirus solutions for Mac on the market, and some are even free (SOPHOS springs to mind). With that in mind, you have absolutely no reason not to protect your expensive machine from malware. There is simply no excuse.
The biggest threat of all
15 Mac-Hardening Security Tips to Protect Your Privacy
Finally, we get to the biggest threat of all. This threat applies to every Mac user, and is a vulnerability that must be protected against by EVERY Mac user – no matter who, or where they are.
These days, surveillance practices are out of hand. Governments, Internet Service Providers (ISPs), corporations, advertisers, and cybercriminals, all want to sniff Internet users’ web traffic.
The reason? Personal data is incredibly valuable because it tells whoever has it everything about you. In fact, it is commonly accepted that data is now a form of currency. For this reason, when an app is “free” the reality is that more often than not this is a lie, and people are simply paying for it by handing over their data (due to overly invasive app permissions agreed to by the end user). Public Wifi is another danger. When connected to a public WiFi hotspot any of the other users attached to the WiFi could potentially sniff your traffic.
VPN is for everyone

Why You Should Connect to a VPN on Mac and iOS — and How To
This surveillance problem is completely unique because it is about the data going from and to your device rather than the data that is inside the machine. For this reason, it applies just as much to an Android user as it does to a Windows, iOS, or Mac OSX user.
VPNs work by sending traffic via a proxy server, and encrypting the data at each point (at least in most services). Encryption naturally helps to protect your data stopping individuals from being able to get at that data. There are also additional benefits, such as being able to access geo-blocked content (watching the shows offered by Netflix in another country).
A VPN is the perfect solution and it is the number one best form of personal cybersecurity available on the market today for every Mac computer. With that said, a word of warning: not every VPN was created equally. Some VPNs provide outdated encryption and have poor privacy policies. Those VPNs are a total waste of money and actually make extra revenue by selling subscriber data to third parties. For this reason, it is important that people don’t fall into a trap. Instead, they should subscribe to a reliable, trusted VPN provider, with a proven track record. The difference between the two is black and white.
The Need to protect yourself
How to protect your Mac against malware
The first step in protecting yourself is to be aware that there is a problem, and that while Macs have historically had a golden era in protection from unintended software, the system isn’t foolproof. It’s imperative that Mac users are both aware of these problems, and that they protect themselves from both malware, and from snooping from other sources. As the market share of Macs grows, the operating system presents itself as a larger, more lucrative target for criminals. Why just go after the Windows users, if there’s an unsuspecting Mac user who hasn’t been wary enough to protect themselves with the multitude of different mechanisms available.




