If you wrote out a list of every type of cyberattack perpetrated it would stretch down the block. Digital information systems are incredibly complex. As a result, there are lots of different weaknesses and vulnerabilities to exploit. For any business trying to get serious about cybersecurity that sounds like troubling news.
Thankfully, the vast majority of attacks are rare, extinct, or ineffective. Companies have more robust defenses when they focus on the most common and consequential threats rather than every threat imaginable.
As you begin to address the issue of cybersecurity in depth, keep these five common attacks top of mind:
1. Corrupted Websites
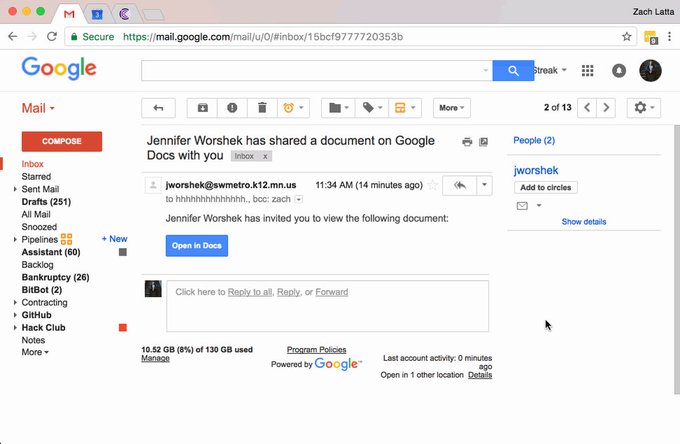
Don’t Fall for This Google Docs Phishing Scam
This is a major source of malware. Users are tricked into visiting a bad website that infects their computer with malicious code. Hackers can even insert this code onto a legitimate website, making it even harder to spot the threat. Since these attacks try hard to mimic the look of familiar and authentic websites they are very effective. And once malware is past the security perimeter and inside the network it can wreak havoc. Food anti-malware and antivirus software is a must for any user.
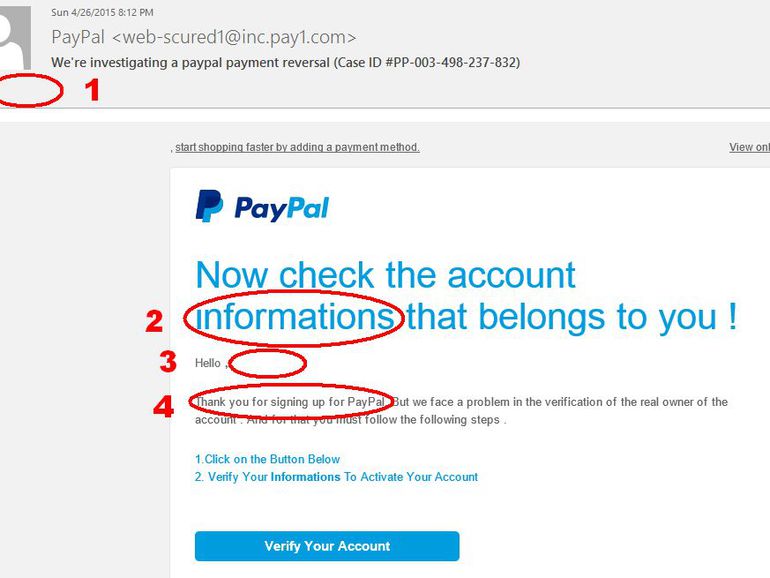
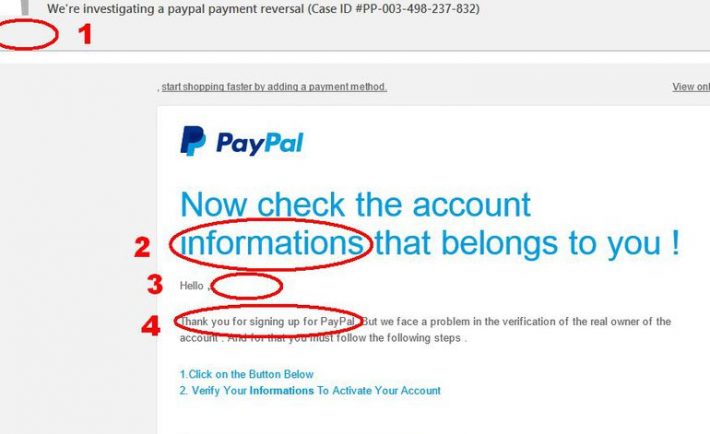
2. Phishing Attacks
These are most common in the form of spam emails. A message appears in the inbox asking users to visit a certain website or provide specific information. Often users are asked to provide login information or other private details. These message look like they are from banks, service providers, coworkers or other trustworthy sources. Only eagle-eyed users spot the red flags such as misspelled brand names or typos, which is why hackers use these attacks so much. The best thing you can do is avoid opening suspicious emails.
3. Unpatched Software

8 best practices for managing software patches
When a company issues a software patch they also publicly admit there is a flaw in the software. Hackers are made instantly aware of where to attack. Most companies will install the patch and eliminate the threat, but not every company will. There are simply too many patches to manage and too few IT resources. Hackers bank on this fact and attack unpatched problems aggressively. To avoid becoming the next victim, turn on auto-updates on all your programs.
4. Advanced Persistent Threats
These are the least common but most aggressive type of attacks. Hackers tailor their tactics based on who they are targeting and what they hope to steal. Then they launch an aggressive attack that strikes over and over. Even if it encounters one roadblock it goes searching for another entry point. That makes defenses very difficult. As companies have tried unsuccessfully to deter these attacks they are looking more seriously at limiting the damage. That is leading them to create disaster response plans, coordinate IT and PR teams, and seek out cyber attack insurance.
5. Social Media Manipulation
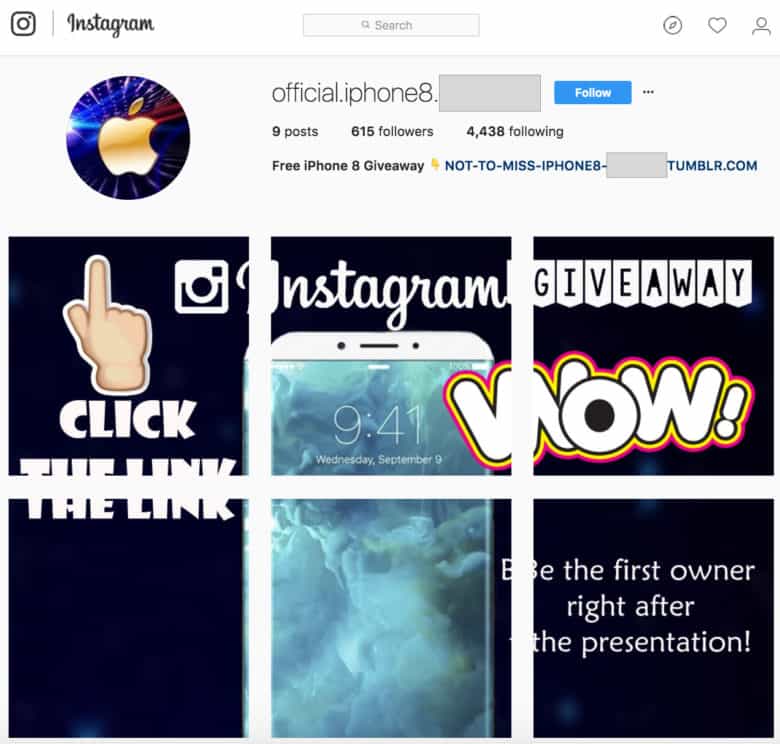
Don’t fall for free iPhone scams on social media
Social media is meant to be fun and familiar. The casual nature of it makes it perfect for hackers to catch people off guard. There are countless different social media scams and schemes that guide users to corrupted websites or dangerous downloads. As more and more of online life takes place on social media platforms this threat is likely to rise up the list. So be careful what you click and with whom you communicate while on social.
Focusing on these five threats does not guarantee perfect cyber security. It does, however, focus resources where they are needed most. In the ongoing battle over cybersecurity, that is the kind of strength and certainty that companies need.