Any company, regardless of its size, can suffer from a security breach or a cyber-attack. In 2020, cyber-attacks increased to 600%, mostly because of the coronavirus pandemic. It’s essential to
For Peace of Mind You Need to Protect Your Business
Being a business owner is a big commitment. From the responsibility to your employees to the need to succeed, there’s a lot of components that go into keeping your business
How Companies Can Build Goodwill Through Tech
It’s important to understand that while goodwill is an important part of building trust with your customers and clients, it’s also changing in modern business life. Sometimes, even being noticed
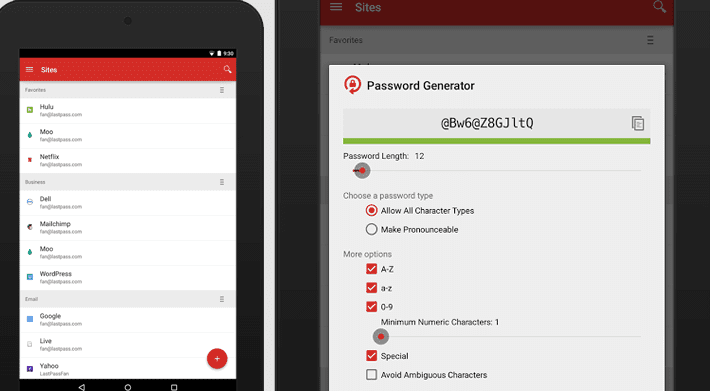
5 Apps That Protect You From Hackers
More and more people are using their mobiles every day. According to Pew Research Center, 77% of Americans now own a smartphone, and the global median of adults who have
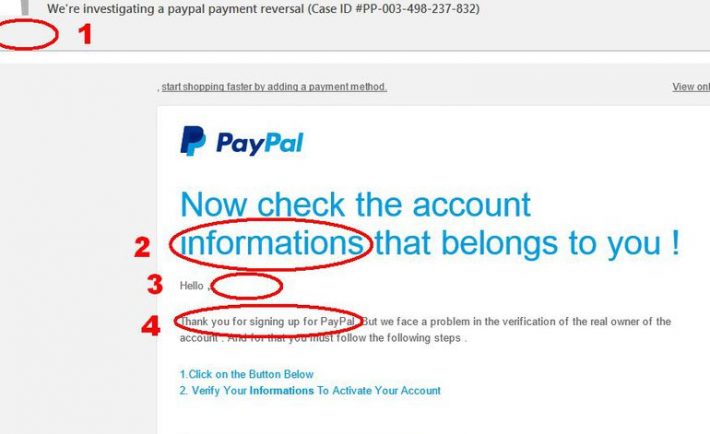
5 Cyber Attacks Businesses Should Fear the Most
If you wrote out a list of every type of cyberattack perpetrated it would stretch down the block. Digital information systems are incredibly complex. As a result, there are lots
How To Create The Best Disaster Recovery Plan For Your Small Business
If your small business is currently not prepared for disaster, then you should seriously consider taking practical steps to ensure you have a Disaster Recovery (DR) plan in place to
Understanding and Handling Big Data for Businesses
You just got used to the term big data and you want to learn more about the topic? Reading this article will make everything clearer. Working with data on a
Are You Taking Your Digital Security Seriously Enough? 4 Shocking Consequences of a Cyber Security Breach
As a business owner, protecting your customer’s sensitive information is of the utmost importance. However, providing a fool-proof data security system for your network isn’t always feasible, because these types