GPS technology is nearly widespread in the current era. Millions of people rely on GPS technology to plan road trips, avoid traffic, and seek roadside help. Most people and organizations
API Security Best Practices: Protecting Your Data
Introduction to API Security API security is a top concern for any organization that exposes its data and services to the world. The best way to protect your API is
For Peace of Mind You Need to Protect Your Business
Being a business owner is a big commitment. From the responsibility to your employees to the need to succeed, there’s a lot of components that go into keeping your business
Employee Training: Cybersecurity at Work
Back in the days, it seemed like robberies and break-ins were the biggest threat to businesses. These days, on the other hand, thieves have way more access to our sensitive
Is Your Organisation at Risk of a Cyber-Attack? 3 Ways to Help you to Find Out
Businesses of all sizes, from small operations to international corporations, are coming to terms with the growing threat of cyber-security. The rate of attacks is rapidly increasing, and hackers are
The New Technology of Crime Fighting
Every day, the world of crime fighting is getting closer to the world of Batman. Look at all of the gear Batman, the world’s greatest detective, has utilized over the
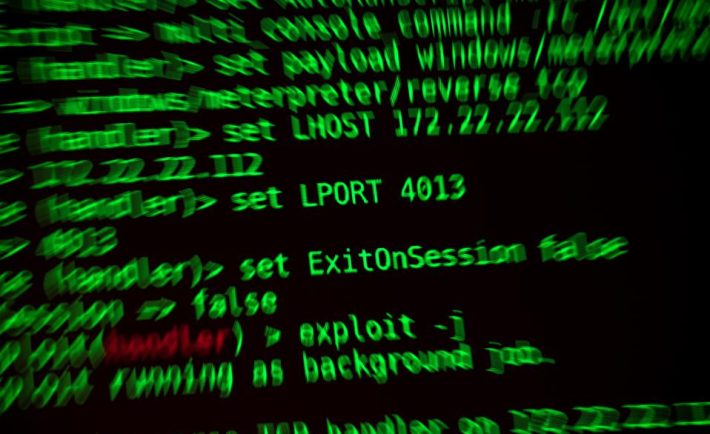
Could You Get Hacked?
Digital crime is on the rise. No longer are hackers just isolated criminals hiding away in basements. They are complete organizations: groups of specialists that are focused on accessing your
The Future of Passwords: Your Body
The requirements of strong passwords is always changing. At the beginning, a few letters or a single word would suffice. The requirements grew to include a specific number of characters,