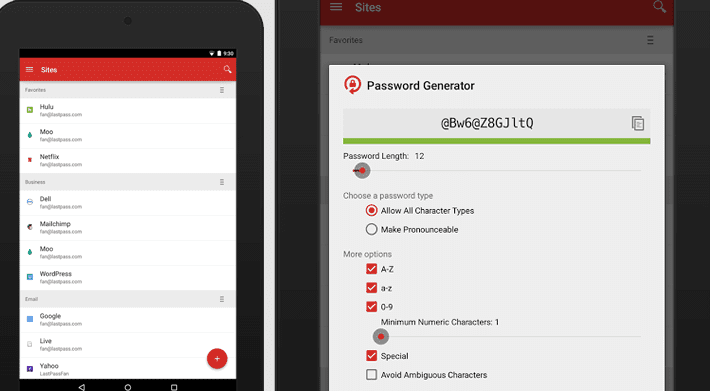
Privilege management is the process of limiting access to resources using controlling privileges. Privileges are rights, permissions, or capabilities granted to users to perform tasks on a computer system. Limiting
5 Apps That Protect You From Hackers
More and more people are using their mobiles every day. According to Pew Research Center, 77% of Americans now own a smartphone, and the global median of adults who have
How Technology is Safeguarding our Data
Personal data, it’s something we hear a lot about on the news. There always appears to be an article, politician, or television show discussing how they want access to personal
The Alternatives to VPNs for Amazing Cyber Security
Hackers today employ a number of innovative ways to secure private data including phishing, Trojans or denial of service (DOS) attacks. Each attack becomes a little more creative than the
How To Stay Safe Online Today
It is important to keep personal information safe online, but many people aren’t sure of exactly how their data is used or how they can go about maintaining privacy when
Why Ecommerce Sites Need to be Trustworthy
Most businesses understand the importance of being trusted by their customers. When you’re handling someone’s personal and financial information, exuding honesty is a must. Therefore, ecommerce sites need to be
Everything you needed to know about the Microsoft Compatibility Telemetry issue
Plenty of people have noticed the Microsoft Compatibility Telemetry in their Windows Task Manager but have no idea what it is. Many users even try to remove it since it