
The line between our digital activities and our real-world lives continues to blur. With the touch of a button there are more ways than ever before to share personal information, making it more important than ever to protect and secure our privacy.
Strong encryption protects us
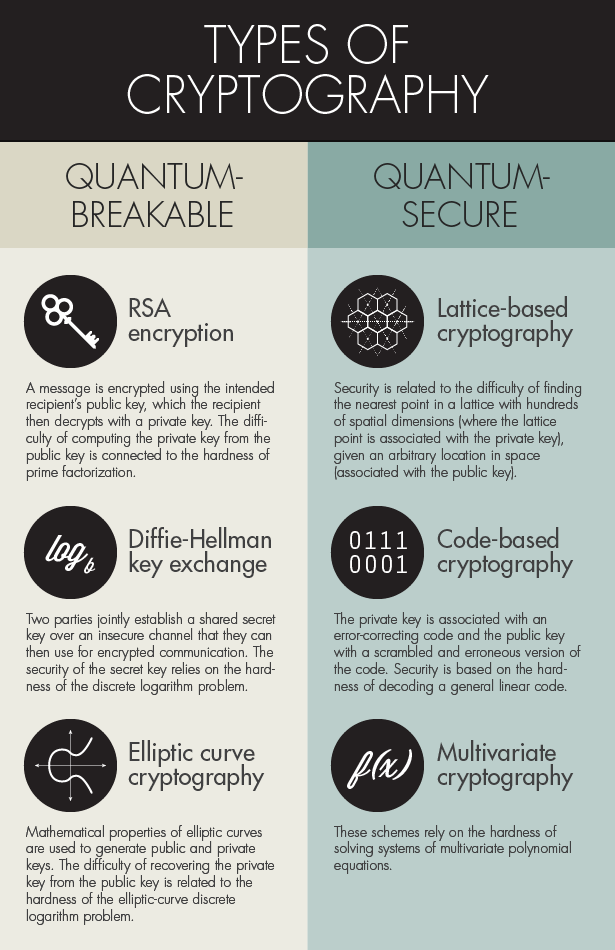
The Tricky Encryption That Could Stump Quantum Computers
Today the “battle” for encryption is a very touchy subject. In light of recent current events and increasingly sophisticated hacking and surveillance tactics, Internet users are demanding the right to protect their personal information with commercial encryption technology – but this isn’t sitting well with many government agencies. Around the world, governments have considered implementing legislation banning encryption above a certain strength for civilian use and forcing jail time for refusing to give the key to your encrypted data during an investigation related to “terrorism.”
Encryption was originally used to protect top secret military information. But in today’s modern, digital marketplace, users need to know that everything from their financial information to their social security numbers and their intimate conversations are protected when they go online. Encryption works with what coders and developers call an encryption algorithm. This is more commonly known as an encryption key. Encryption keys make information unreadable or unobtainable. A decryption key is needed to be able to access this information and view it normally. This is what is so important in cyberhacking cases. The decryption key is so important to investigators that they are willing to put people away for up to 5 years or more in order to obtain the information that they might need.
Security needs to be checked at all levels

SHA1 algorithm securing e-commerce and software could break by year’s end
Everyday we make important, life-changing decisions over the Internet. The encryption of these activities, these individual data points, is very important, and any lack of encryption can cause major problems. For example, Target’s shoddy encryption standards allowed hackers to get the credit card information of thousands of shoppers in a high-profile 2013 data breach. Financial information can disappear in an instant if it isn’t protected, and that’s not all. According a top securities website, home surveillance cameras connected to the Internet have the greatest number of security vulnerabilities of any new automated technology – leaving users open to attacks both online and off. In recent demos, major security flaws have been found in millions of smartphones, allowing hackers to gain access with just the knowledge of a certain individual’s phone number.
However, there are many heated debates right now in society about how far encryption should go. The US government mainly is very concerned with being able to see any and all information that is going into and coming out of electronic devices. Companies and consumers on the other hand are concerned that this is an invasion of privacy. Apple has been fighting against encryption laws for quite some time now. When Apple refused to unlock an iPhone related to the San Bernardino shooting tragedy, they stated that they would be setting a dangerous precedence for the security of iPhones in the future.
It will be interesting to see how the ongoing debate regarding encryption unfolds in the future. It is important for individuals to feel that they are safe from cyber hacks and cyber terrorists, but it is also important that they feel their privacy is being protected. It is a fine line that lawmakers and technology developers must walk in order to fulfill both needs fairly and effectively.





One comment
Leave a reply →
Comments are closed.